Android的AES加密盘块损坏Android、AES
我使用的方法如下,如果我进入右键一切工作正常。 但是,如果我输入了错误的键,我收到一个BadPaddingException:垫块损坏... 难道我做错了什么?
公共无效initKey(字符串passwd文件,byte []的盐)抛出抛出:NoSuchAlgorithmException,InvalidKeySpecException,NoSuchProviderException {
byte []的localsalt =盐;
PBEKeySpec密码=新PBEKeySpec(passwd.toCharArray(),localsalt,1024,128); //,localsalt,1000,128); // 128bit的AES ENC
SecretKeyFactory工厂= SecretKeyFactory.getInstance(PBEWithMD5And128BitAES-CBC-OpenSSL的,BC);
PBEKey调用键=(PBEKey调用)factory.generateSecret(密码);
encKey =新SecretKeySpec(key.getEn codeD(),AES);
}
公共字符串txt2enc(字符串etxt)抛出抛出:NoSuchAlgorithmException,NoSuchPaddingException,InvalidKeyException将,IllegalBlockSizeException,BadPaddingException,UnsupportedEncodingException {
最后密码加密= Cipher.getInstance(AES); // AES
cipher.init(Cipher.ENCRYPT_MODE,encKey);
byte []的加密= cipher.doFinal((etxt).getBytes(UTF-8));
返回Base64.en codeToString(加密,0);
}
//解密
公共字符串txt2dec(字符串dtxt)抛出InvalidKeyException将,抛出:NoSuchAlgorithmException,NoSuchPaddingException,IllegalBlockSizeException,BadPaddingException,UnsupportedEncodingException {
最后密码加密= Cipher.getInstance(AES);
cipher.init(Cipher.DECRYPT_MODE,encKey);
byte []的解密= cipher.doFinal(Base64.de code(dtxt,0));
返回新的String(解密); //返回Base64.en codeToString(解密,0);
}
解决方案
你没有做错什么。它的预期。这在技术上是的Java加密问题(这似乎并不很容易找到)的副本。看到这个回答一个很好的解释。可以考虑增加一个MAC(消息认证code)安全地完成更多的东西像一个校验和。
I am using the methods below and if I enter the right key everything works fine. But if I enter a wrong key I am receiving a BadPaddingException:pad block corrupted... Am I doing something wrong?
public void initKey(String passwd, byte[] salt) throws NoSuchAlgorithmException, InvalidKeySpecException, NoSuchProviderException{
byte[] localsalt = salt;
PBEKeySpec password = new PBEKeySpec(passwd.toCharArray(),localsalt, 1024,128);//, localsalt, 1000, 128); //128bit enc aes
SecretKeyFactory factory = SecretKeyFactory.getInstance("PBEWithMD5And128BitAES-CBC-OpenSSL","BC");
PBEKey key = (PBEKey) factory.generateSecret(password);
encKey = new SecretKeySpec(key.getEncoded(), "AES");
}
public String txt2enc(String etxt) throws NoSuchAlgorithmException, NoSuchPaddingException, InvalidKeyException, IllegalBlockSizeException, BadPaddingException, UnsupportedEncodingException {
final Cipher cipher = Cipher.getInstance("AES");//AES
cipher.init(Cipher.ENCRYPT_MODE, encKey);
byte[] encrypted = cipher.doFinal((etxt).getBytes("UTF-8"));
return Base64.encodeToString(encrypted, 0);
}
//decryption
public String txt2dec(String dtxt) throws InvalidKeyException, NoSuchAlgorithmException, NoSuchPaddingException, IllegalBlockSizeException, BadPaddingException, UnsupportedEncodingException{
final Cipher cipher = Cipher.getInstance("AES");
cipher.init(Cipher.DECRYPT_MODE, encKey);
byte[] decrypt = cipher.doFinal(Base64.decode(dtxt, 0));
return new String(decrypt);//return Base64.encodeToString(decrypt, 0);
}
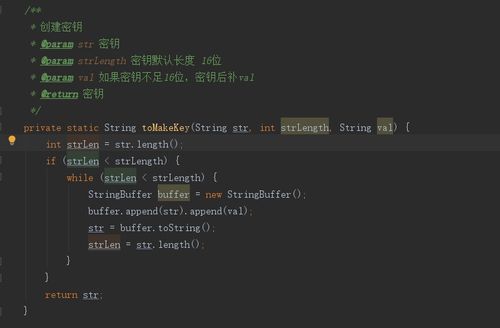
解决方案
You're not doing anything wrong. It's expected. This is technically a duplicate of Java Encryption issue (which doesn't seem to be easy to find). See this answer for a good explanation. You can consider adding a MAC (Message Authentication Code) to safely accomplish something more like a checksum.







