如何安全是的SQLite和共享preferences在Android上的文件?是的、文件、安全、SQLite
首先,一点我的背景。我一直在大型网站系统了十多年,Android的是我一直在寻找在过去两个月;你可以想像,差距是相当广泛:)
纵观Android的安全和权限和的文件的数据存储部分,直接对话开发商,阅读书籍和教程,它是pretty的不清楚整个样板工程。但是,我无法找到答案的SQLite和共享preferences文件是否足够安全的存储精致的未加密信息(例如,OAuth的令牌)。是否有可能有人抓住他们以任何方式?引用Android的文档:
由应用存储的任何数据都将被分配该应用程序的用户ID,并且通常不访问其他包。
这是的无法正常访问的一部分,给了我更多的白发:)
感谢您,乐于助人的答案是AP preciated:)
解决方案是否有可能有人抓住他们以任何方式?
这要看别人。由于波罗夫先生表示,扎根手机用户可以在任何他们想要的。普通用户和其他应用程序无法在默认情况下。
这是不能正常访问的一部分给了我额外的白发:)
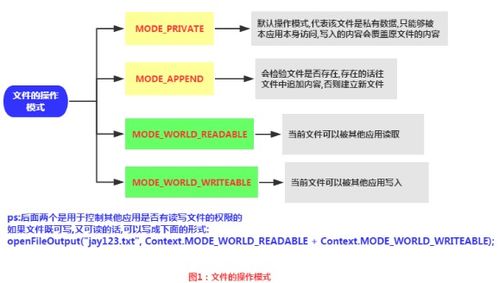
在默认情况下,文件是安全的。你可以让他们的世界可读或可写的,如果你选择。
那岂不是可以反编译apk文件,找到加密密钥,以及在这种情况下?
这取决于你正在抵御谁。如果你是抵御其他应用程序,让用户提供加密密钥。如果你是防御用户,你就完蛋了,就像DRM的所有实现都搞砸了。
First, a bit of my background. I have been working on large web systems for over a decade, Android is something I have been looking at for the past two months; as you can imagine, the gap is quite wide :)
Looking at Android's Security and Permissions and Data Storage part of documentation, talking directly to developers, reading books and tutorials, it is pretty clear how entire model works. However, I was unable to find an answer whether SQLite and SharedPreferences files are secure enough to store delicate non-encrypted information (for example, OAuth tokens). Is it possible for someone to grab them in any way? Quoting Android's documentation:
Any data stored by an application will be assigned that application's user ID, and not normally accessible to other packages.
It's the not normally accessible part giving me additional grey hair :)
Thank you, helpful answers are appreciated :)
解决方案Is it possible for someone to grab them in any way?
That depends on the someone. As Mr. Burov indicates, users of rooted phones can get at whatever they want. Ordinary users and other applications can't, by default.
It's the not normally accessible part giving me additional grey hair :)
By default, files are secure. You can make them world-readable or world-writable if you choose.
Wouldn't it be possible to decompile apk file and find encryption key as well in that case?
That depends on who you are defending against. If you are defending against other apps, have the user supply the encryption key. If you are defending against the user, you're screwed, just as all implementations of DRM are screwed.










